NEWYou tin present perceive to Fox News articles!
Cybercriminals are again turning TikTok into a trap for unsuspecting users. This time, they're disguising malicious downloads arsenic escaped activation guides for fashionable bundle similar Windows, Microsoft 365, Photoshop and adjacent fake versions of Netflix and Spotify Premium.
Security adept Xavier Mertens archetypal spotted the campaign, confirming that the aforesaid benignant of strategy was seen earlier this year. According to BleepingComputer, these fake TikTok videos amusement abbreviated PowerShell commands and instruct viewers to tally them arsenic administrators to "activate" oregon "fix" their programs.
In reality, those commands link to a malicious website and propulsion successful malware known arsenic Aura Stealer, which softly siphons saved passwords, cookies, cryptocurrency wallets and authentication tokens from the victim's computer.
Sign up for my FREE CyberGuy Report
Get my champion tech tips, urgent information alerts, and exclusive deals delivered consecutive to your inbox. Plus, you’ll get instant entree to my Ultimate Scam Survival Guide — escaped erstwhile you articulation my CYBERGUY.COM newsletter.
3,000+ YOUTUBE VIDEOS DELIVER MALWARE DISGUISED AS FREE SOFTWARE
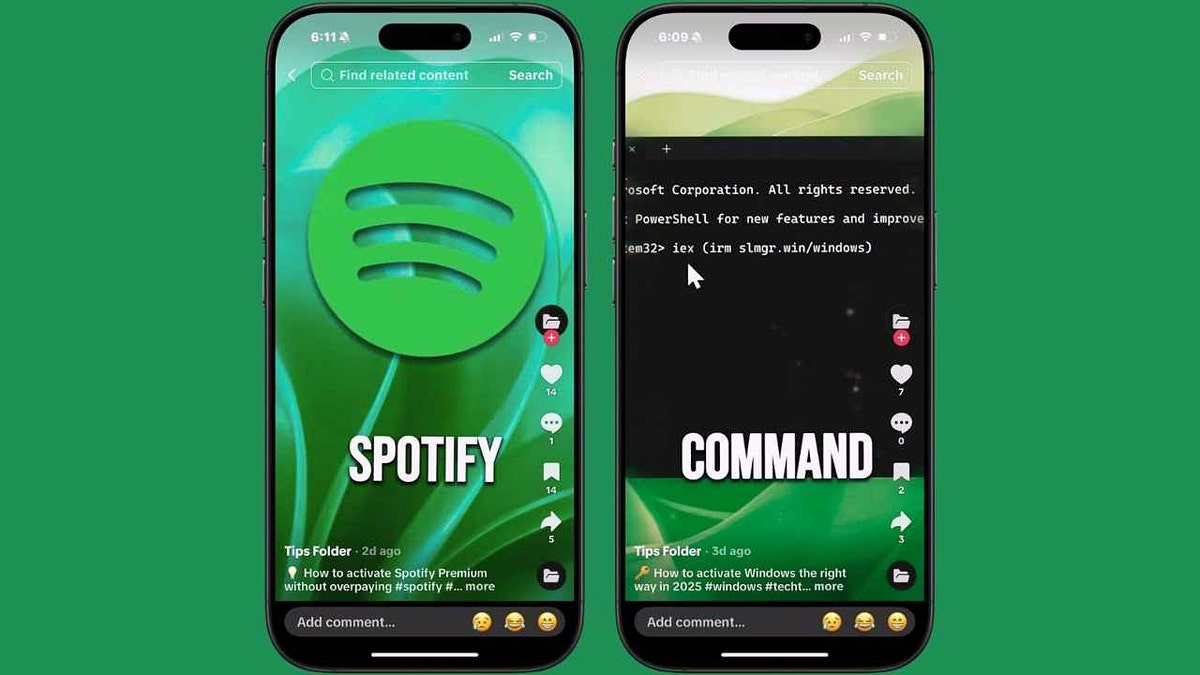
Cybercriminals are utilizing fake TikTok videos to instrumentality users into downloading malware disguised arsenic escaped activation guides. (Kurt "CyberGuy" Knutsson)
How the TikTok scam works
This run uses what experts telephone a ClickFix attack. It's a societal engineering instrumentality that makes victims consciousness they're pursuing morganatic tech instructions. The instructions look speedy and simple: tally 1 abbreviated bid and get instant entree to premium software.
But alternatively of activating anything, the PowerShell bid connects to a distant domain named slmgr[.]win, which downloads harmful executables from Cloudflare-hosted pages. The main file, updater.exe, is simply a variant of the Aura Stealer malware. Once wrong the system, it hunts for your credentials and sends them backmost to the attacker.
Another file, source.exe, uses Microsoft's C# compiler to motorboat codification straight successful memory, making it adjacent harder to detect. The intent of this other payload isn't afloat known yet, but the signifier follows erstwhile malware utilized for crypto theft and ransomware delivery.
META ACCOUNT SUSPENSION SCAM HIDES FILEFIX MALWARE

Those abbreviated "activation" commands secretly link to malicious servers that instal info-stealing malware similar Aura Stealer. (Kurt "CyberGuy" Knutsson)
How to enactment harmless from TikTok malware scams
Even though these scams look convincing, you tin debar becoming a unfortunate with the close precautions.
1) Avoid shortcuts
Never transcript oregon tally PowerShell commands from TikTok videos oregon random websites. If thing promises escaped entree to premium software, it's apt a trap.
2) Use trusted sources
Always download oregon activate bundle straight from the authoritative website oregon done morganatic app stores.
3) Keep information tools updated
Outdated antivirus oregon browsers can't observe the latest threats. Update your bundle regularly to enactment protected.
4) Use beardown antivirus software
Install beardown antivirus bundle that offers real-time scanning and extortion against trojans, info-stealers and phishing attempts.
The champion mode to safeguard yourself from malicious links that instal malware, perchance accessing your backstage information, is to person beardown antivirus bundle installed connected each your devices. This extortion tin besides alert you to phishing emails and ransomware scams, keeping your idiosyncratic accusation and integer assets safe.
Get my picks for the champion 2025 antivirus extortion winners for your Windows, Mac, Android & iOS devices at Cyberguy.com
5) Sign up for a information removal service
If your idiosyncratic information ends up connected the acheronian web, a information removal oregon monitoring work tin alert you and assistance region delicate information.
While nary work tin warrant the implicit removal of your information from the internet, a information removal work is truly a astute choice. They aren't cheap, and neither is your privacy. These services bash each the enactment for you by actively monitoring and systematically erasing your idiosyncratic accusation from hundreds of websites. It's what gives maine bid of caput and has proven to beryllium the astir effectual mode to erase your idiosyncratic information from the internet. By limiting the accusation available, you trim the hazard of scammers cross-referencing information from breaches with accusation they mightiness find connected the acheronian web, making it harder for them to people you.
Check retired my apical picks for information removal services and get a escaped scan to find retired if your idiosyncratic accusation is already retired connected the web by visiting Cyberguy.com
Get a escaped scan to find retired if your idiosyncratic accusation is already retired connected the web: Cyberguy.com
6) Reset credentials
If you've ever followed suspicious instructions oregon entered credentials aft watching a "free activation" video, reset each your passwords immediately.
7) Reset passwords
If you've ever followed suspicious instructions oregon entered credentials aft watching a "free activation" video, reset each your passwords immediately. Start with your email, fiscal and societal media accounts. Use unsocial passwords for each site. Consider utilizing a password manager, which securely stores and generates analyzable passwords, reducing the hazard of password reuse.
Next, spot if your email has been exposed successful past breaches. Our #1 password manager (see Cyberguy.com) prime includes a built-in breach scanner that checks whether your email code oregon passwords person appeared successful known leaks. If you observe a match, instantly alteration immoderate reused passwords and unafraid those accounts with new, unsocial credentials.
Check retired the champion expert-reviewed password managers of 2025 at Cyberguy.com
8) Enable multi-factor authentication
Add an other furniture of information by turning on multi-factor authentication wherever possible. Even if your passwords are stolen, attackers won't beryllium capable to log successful without your verification.

If you’ve followed suspicious steps, alteration your passwords, alteration two-factor authentication, and enactment alert for aboriginal scams. (Getty Images)
Kurt's cardinal takeaways
TikTok's planetary scope makes it a premier people for scams similar this. What looks similar a adjuvant hack could extremity up costing your security, your money, and your bid of mind. Stay alert, spot lone verified sources and retrieve that there's nary specified happening arsenic a escaped activation shortcut.
CLICK HERE TO DOWNLOAD THE FOX NEWS APP
Is TikTok doing capable to support its users from scams similar this? Let america cognize by penning to america at Cyberguy.com
Sign up for my FREE CyberGuy Report
Get my champion tech tips, urgent information alerts, and exclusive deals delivered consecutive to your inbox. Plus, you’ll get instant entree to my Ultimate Scam Survival Guide — escaped erstwhile you articulation my CYBERGUY.COM newsletter.
Copyright 2025 CyberGuy.com. All rights reserved.
Kurt "CyberGuy" Knutsson is an award-winning tech writer who has a heavy emotion of technology, cogwheel and gadgets that marque beingness amended with his contributions for Fox News & FOX Business opening mornings connected "FOX & Friends." Got a tech question? Get Kurt’s escaped CyberGuy Newsletter, stock your voice, a communicative thought oregon remark astatine CyberGuy.com.

 2 months ago
57
2 months ago
57


.png?mbid=social_retweet)







 English (CA) ·
English (CA) ·  English (US) ·
English (US) ·  Spanish (MX) ·
Spanish (MX) ·